
Automatically apply for jobs with Zippia
Upload your resume to get started.
Senior information assurance engineer skills for your resume and career
15 senior information assurance engineer skills for your resume and career
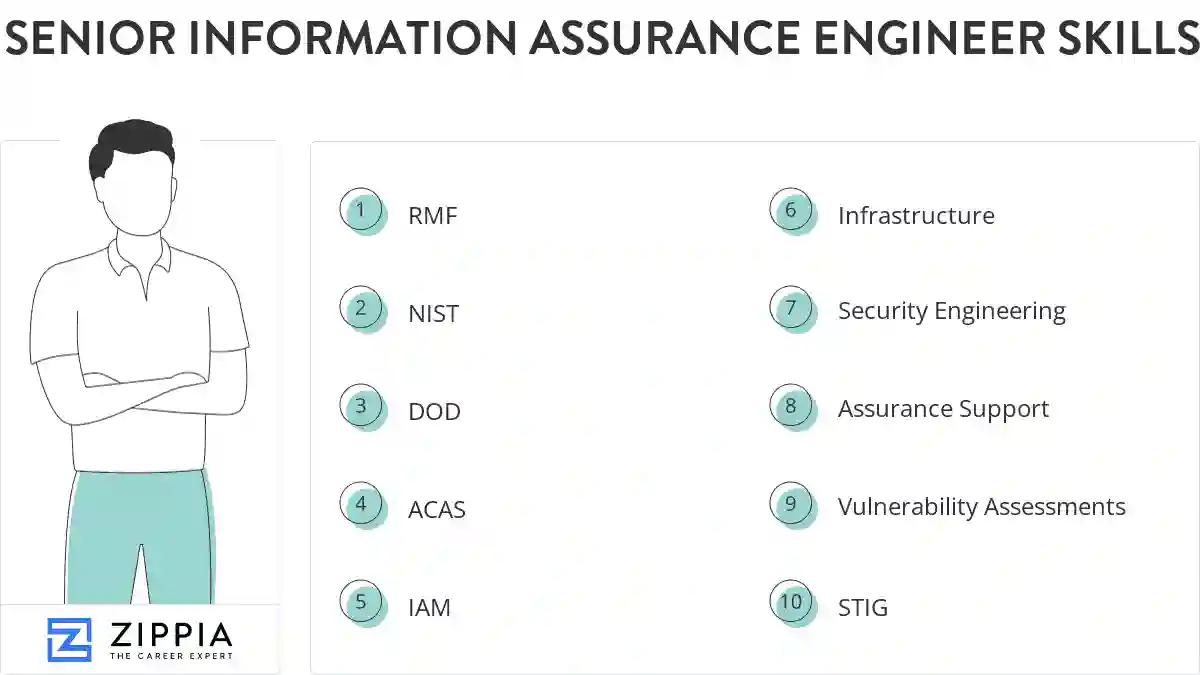
1. RMF
RMF (the Risk Management Framework) refers to a set of criteria used by the federal government and its contractors to improve information security. To be proficient in RMF, in-depth technical experience with core technologies like Digital, Cloud, Data Protection, etc., along with knowledge of FISMA and FedRAMP regulatory compliance requirements.
- Attended 5-day instructor led Risk Management Framework (RMF) course.
- Prepare security assessment package recommending system for or against authorization to operate using DIACAP and RMF process
2. NIST
- Examined application ST&E and SR/FR testing methods and identified gaps with testing of NIST SP 800-53 Rev.4 security controls.
- Experience and understanding of the National Institute of Standards and Technology (NIST) Joint Task Force Transformation Initiative documents.
3. DOD
Definition of Done (DoD) is a set of deliverables that are needed to devise software. These deliverables are valuable to the system and can be exemplified by writing code, coding comments, unit testing, integration testing, design documents, release notes, and so on.
- Updated System Security Authorization Agreement documentation to reflect current DoD infrastructure, to include Contingency/Disaster Recovery Plans.
- Supported DoD clients with application and software architecture assessments, risk analysis, and vulnerability assessments.
4. ACAS
- Utilize ACAS and HBSS tools to analyze/monitor Vulnerability analysis scan results.
- Update ACAS plugins weekly or when updates became available on the DISA provided website.
5. IAM
IAM policies are specific permissions on the Amazon Web Server (AWS) for an operation or action regardless of the way it is performed. For example, if an IAM policy defines GetUser action, then a user can get user information from any parts of the AWS, such as the AWS Management Console, AWS API, or the AWS CLI.
- Maintained databases of system accreditation status, developed reports, and alerted the MDA IAM when accreditation documentation required updating.
- Coordinate security procedures with the IAM and initiate investigative procedures for security incidents.
6. Infrastructure
Infrastructure includes the organizational and physical structures needed to run an area or a society smoothly. It is a group of basic facilities required for any society or firm to run sustainably and efficiently. The infrastructural system is a high investing area and helps majorly in flourishing the economy and prosperity of a country. It is an underlying system needed for ensuring the safety and comfort of the public and to run a country smoothly. All the tasks needed to be performed for a flourishing economy and a happy and healthy public are included in infrastructure.
- Utilized Adaptive Authentication/Access infrastructure to perform audits of enterprise systems and information management processes to identify breaches.
- Provide security solutions and evaluates the impact new or updated systems have on the security infrastructure.
Choose from 10+ customizable senior information assurance engineer resume templates
Build a professional senior information assurance engineer resume in minutes. Our AI resume writing assistant will guide you through every step of the process, and you can choose from 10+ resume templates to create your senior information assurance engineer resume.7. Security Engineering
Security engineering is the prevention of misuse and malicious behavior in an application or organization. Security engineering skills include designing, maintaining, updating systems security controls and countermeasures. Monitoring systems for security incidents, including preventing unauthorized access, policy breaches, and third-party unauthorized access into systems, is part of this skill set.
- Provided Information System Security Engineering support for program execution and new business pursuits on Net-Centric communication systems.
- Managed 3 IA analyst in conducting Vulnerability Management, Security Engineering, Certification and Accreditation, and Computer Network Defense activities.
8. Assurance Support
- Provided information assurance support for the development and implementation of security architectures to meet new and evolving security requirements.
- Provided Information Assurance Support in preparing and delivering briefs to senior level IT professionals across multiple locations.
9. Vulnerability Assessments
- Provide engineering and technical assistance to perform cyber vulnerability assessments.
- Assisted IT network managers and technicians in developing procedures for conducting risk and vulnerability assessments of IT networks.
10. STIG
- Perform analysis of systems for STIG and IAVA compliance.
- Created STIG processes of servers and workstations.
11. Risk Assessments
The process of analyzing and identifying the acts or events that have the potential to negatively affect an individual, asset, or business is called risk assessment. Risk assessments are important because they form an integral part of an organization as well as occupational safety plans
- Trained new personnel in Risk Assessments, EMSEC/TEMPEST, and Vulnerability Management.
- Provided Information Assurance assistance and consulting in regards to conducting Risk Assessments.
12. Disa
- Directed the use of DISA Gold Disk, SRR Scripts, and Retina Scans used in conjunction to mitigate system vulnerabilities.
- Ensured Time Compliance Network Order (TNCO) effectiveness through the implementation of patch management and use of DISA GoldDisk.
13. Security Policies
- Collaborated with customers to identify system security requirements, implement security policies, and coordinate successful approvals to operate the systems.
- Participated in network and systems design to ensure proper implementation of security policies.
14. Security Posture
- Assist the organization with improving the security posture and compliance with required information assurance measures through training and development.
- Developed, revised, and monitored network policies and procedures to ensure standardized processes for maintaining security posture.
15. Linux
Linux is a Unix-like operating system. Just like Windows, Mac OS, and IOS, Linux is an operating system used by millions across the globe. Android itself is powered by the Linux operating system. Linux manages all the hardware resources that are associated with your computer. The software is famous because of the protection it grants from viruses, malware, and crashes. The Linux operating system is entirely free and is an open-source software meaning it can be altered by those equipped with the knowledge to code.
- Maintained and deployed Linux based Network Allocated Storage (NAS) boxes in many environments.
- Assist with system hardening within the Windows and Linux server environment.
5 Senior Information Assurance Engineer resume examples
Build a professional senior information assurance engineer resume in minutes. Browse through our resume examples to identify the best way to word your resume. Then choose from 5+ resume templates to create your senior information assurance engineer resume.
What skills help Senior Information Assurance Engineers find jobs?
Tell us what job you are looking for, we’ll show you what skills employers want.
What skills stand out on senior information assurance engineer resumes?
David Garaventa
Director, Computer Information Systems and Cybersecurity Programs, Assistant Professor, CIS, Albertus Magnus College
List of senior information assurance engineer skills to add to your resume
The most important skills for a senior information assurance engineer resume and required skills for a senior information assurance engineer to have include:
- RMF
- NIST
- DOD
- ACAS
- IAM
- Infrastructure
- Security Engineering
- Assurance Support
- Vulnerability Assessments
- STIG
- Risk Assessments
- Disa
- Security Policies
- Security Posture
- Linux
- ATO
- Nessus
- SME
- HBSS
- System Security
- Scap
- Accreditation Process
- FISMA
- Encryption
- Incident Response
- Adaptive
- ICD
- Windows Server
- National Security
- Configuration Management
- Xacta
- Test Procedures
- Retina
- ISSO
- Computer System
- SharePoint
- Switches
- Unix
- ISSM
- Data Loss Prevention
- Emerging Technologies
- Workstations
- System Certification
- IAVA
- NSA
- Computer Network
- Security Documentation
Updated January 8, 2025